This is a long one cause there's a lot to talk about. There's a Table of Contents you can use to jump between different topics if you want, or you can just listen to the audio.
So my 2026 started off with a banger. On the evening of New Year's Day while watching TV with my girlfriend, my long-standing Discord account and community server were compromised by a hacker (herein known as "the scumbag"), who held them for ransom and ultimately defaced them when I wouldn't pay. Unfortunately, this is common on Discord, but I was particularly confused by this incident because as a risk-averse IT guy, I had all the account safeguards in place that you're supposed to. You hear about this happening to others and don't tend to think much of it but in the painfully long process of dealing with it, I've learned a number of things about both Discord and the platforms used to spread these hacks and how lacking many of them are in both security and support.
I'm going to detail what happened, some tips on how you can prevent it happening to you, and the unfortunate things I've learned along the way. My hope is both to get this off my chest and also educate some of you to better protect your own presences on this platform that's basically a monopoly.
How It Started

First off, I want to be clear that aside from the scumbag himself, this is ultimately my fault. I should have been more vigilant and were I not so tired at the time, I might have been. As I'll discuss later, Discord could have done more to prevent this and make it easier to fix, but I'm still the one who fell for the trap.
My girlfriend and I usually make a point of not using other devices while watching TV together, but we were re-watching Fallout season 1, so I was doing some work for a client on my laptop. An indie game dev I know DM'd me asking how I was doing. I hadn't talked to him in a while, but that wasn't unusual. It turns out that he'd also been hijacked and this was the scumbag trying to phish me. The guy even spoke like the dev does, which is how he really got me. He said he was developing a new game with some friends and asked if I'd like to try an early build. He linked me to a web site for the game that not only looked legit, but like something this dev could have been working on.
Without thinking, I clicked the Download button, which proceeded to grab a file hosted on Dropbox. Not unusual for this type of thing. It was a RAR file which is a format rarely used these days, but this dev is old school so I didn't think much of it. In it was an EXE for the installer, which I just ran with no second thought. An installer did pop up, but didn't have any of the prompts you'd typically see, instead just showing a progress bar, which filled quickly, then exiting. Windows Defender never indicated there was anything wrong and as it turns out, no other anti-virus would have either, but more on that later.
Within a few seconds of the installer completing, both Discord and my Chrome browser restarted on their own and my laptop's fans spun up. I instantly knew what happened and hit the hotkey for airplane mode, while also turning the air around me blue, calling myself every name in the book knowing what I just fell for. Unfortunately, as quick as I was to cut the connection, it wasn't quick enough.
What Happened Next
The scumbag messaged me again, asking if the game installed. My laptop was now offline, but I still had Discord on my phone. Thinking it was still the game dev, I told him his site had been hacked and was serving malware. He told me to change my Discord password, but this was a red herring to distract me. He was already in my account. By the time I got to my main PC, I was booted out and couldn't log back in. When I tried to get a password reset, the expected email never arrived.
Trying again a few minutes later, the email did arrive, but when I reset my password and logged in, I was on a burner account with random details, no avatar and wasn't joined to any servers. The scumbag had changed the email address on my main account and then changed a burner account he had in waiting to mine. I wasn't sure how he did this without me confirming it, but that would have to wait.
I immediately went to Discord's support site to open a ticket. They use Zendesk and it has separate credentials from your main account. I had one and tried to login, but found that MFA (multi-factor authentication) had been enabled. I didn't even know their support site had an MFA option. I quickly realized he got in there too, so I went into Google Workspace which hosts my email and added an alias to my main address so I could make a new support account. Part way through filling out a ticket, I get logged out of the site and find that the new account suddenly had MFA enabled too.
My heart sank because I knew how he was doing this and also why I never saw an email from Discord asking to confirm changing my account's email address. He'd also gotten into my Google Workspace email (which is just Gmail hosted on your own domain) and blocked Discord's support address so that the verification went to my junk folder, hiding it from view until it was too late. I promptly went into the admin site, kicked out all active sessions and reset my password, MFA and passkey for it. He thankfully never got back in to that.

I then got a text from my bank telling me that a $260 charge had been made on my main credit card from a place they didn't recognize and they asked me to confirm it. I made sure the text was legit and then said no, causing them to lock my card. It was from a clearly criminal site in Hong Kong that sells Roblox items. Better still, the scumbag used my email address to make the account so I got the purchase confirmation and even a transcript of a support chat he opened when he didn't get the item quick enough. Given the nature of how he got into my laptop, I'm still unsure how he got my credit card details because he only got one. The only thing I can think of was that the crooked Roblox marketplace supported Google Pay, which he would have access to before I kicked him out of Workspace.
At this point, I was freaking out because I didn't know what else he got into. If he got into my password manager, my entire life was compromised. I booted all sessions and reset everything on that too and I'm happy to say that he never got into it or seemingly anything else. It took a couple of hours before I was comfortable concluding that, but nothing weird has happened since. This is where I'm really glad I have the professional knowledge of this stuff I do. I can't imagine the Hell it would be for someone not in IT.
Fuck You, Pay Me
It wasn't enough he stole my account and bought stuff with my credit card. Oh no for you see, everything is a business opportunity now.

The scumbag sent me an email about an hour later eloquently titled "YOU HACKED". Clearly, I was dealing with a master of English standard here. He said I had to respond to him or he would leak and delete everything.
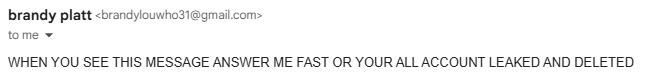
There is nothing incriminating or sensitive to leak from my account, I'm not Dr. Disrespect or anything. However, he also had the only admin account for my Discord server and could do some real damage. When you delete something from Discord, it's gone for good. He never let on that he got into anything else, but also said that I shouldn't bother trying to login to my support account. I already knew he had gotten into my email, but had evicted him from it by this point.
I decided what the Hell, I might as well find out what he wants so I asked. He said he'd hand everything back if I gave him $350USD.
I had already texted a friend to warn people in my server about the hack and he did, but then it disappeared from his client. Turns out, the scumbag was banning anyone who posted a warning. At the time, I didn't know this and thought he already deleted the server so I asked for proof of life and he provided a screenshot. It wasn't timestamped, but he further graced me with his poetry in the message field, which was proof enough for the moment.
From this point, I purposefully delayed my responses to try to keep him on the leash while I submitted a Discord support ticket through yet another email alias, which I now knew he couldn't lock out since I'd booted him from Google. I had a bit of hope that I could get him to slip up and reveal something identifying, but he didn't and has clearly done this a lot. Eventually I asked him how I would pay him were I to and he said with a gift card to the Binance crypto exchange. You can't actually buy Binance gift cards, but you can go to other scummy sites and buy a "redemption code", not unlike a Steam key. He sent me a link to one of these.
It turns out he didn't actually want $350USD, he wanted $350USDT, which is the Tether "stablecoin". Don't worry about trying to understand what that is because all crypto is a scam. However, $350USDT was a downright bargain for me, costing only $46CDN through the link he sent me. Not quite sure how that works as stablecoins are supposed to be pegged to the US Dollar but like I said, all a scam. You actually can't buy these in Canada because we actually regulate financial products up here, but a VPN would have easily worked around that.
Thing is, I don't care if he wanted $1,000 or $1. One of the first rules in this situation is that you never, ever negotiate with terrorists. You give in, you embolden them to victimize others. Yeah, me refusing to pay him makes no real difference, but I'm a man of principal and I'll be damned to Hell and back before I put a capitulation like that on my conscience. Fuck him straight into the sun.
I kept stringing him along but he was starting to get impatient and people I knew who were still in my server said channels were starting to disappear and users were getting randomly banned. He was trying to do the virtual equivalent of sending me severed thumbs in the mail.
I finally wrote back and said there's a million places to buy those gift codes and since he already put $260 on my credit card and I knew he was purging the server, I owed him $90 at best. He didn't much care for that.
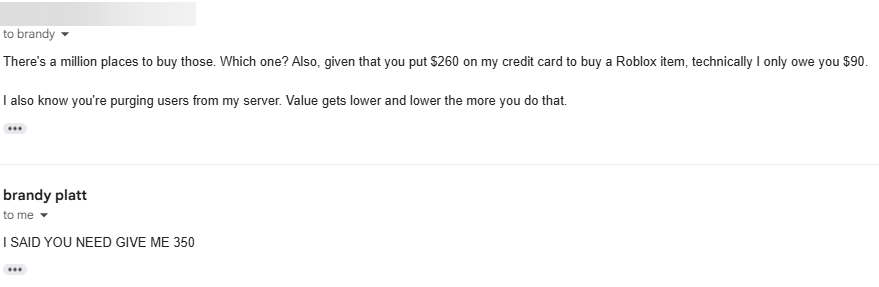
The next day, he told me he saw a post I made on Bluesky about this (I posted links in my server all the time so finding my profile was easy) and that if I didn't pay him that day, he'd delete everything. I lied and said he compromised my only credit card and I would have to wait for the bank to replace it before I could buy the Binance code. He said he didn't care and to find another way. I didn't reply and later that day, he said he was deleting everything.
I learned shortly afterward that he actually can't, at least not entirely. He can ban everyone in my server and delete all the content, but it turns out that you can't delete a server itself without providing an MFA code from its managing account, and he didn't have my key. He also couldn't delete my account while it was still managing a server, so I got a small reprieve there. Unfortunately, that didn't stop him from continuing to use it to try and phish others. Several people told me he tried and one almost fell for it, but he thought to confirm with me at the last minute.
Still, much damage has been done. He deleted all the text channels on my server, all my group chats had been closed and several other servers banned me for trying to phish their users. I don't have a way to reach people from most of them either. I'm going to have to rebuild a lot and that sucks, but it's still better than giving this piece of shit a single dime.
How He Got In (aka Why Electron Sucks Ass)
Being in IT, I'm rather security conscious and had both MFA and a passkey on my account which by the way, you should too. So then how did the scumbag get into my account?
His malware utilized what's called a session hijack. I recommend reading up on them as they're becoming increasingly common, but the short version is that the malware captured the IDs of the Discord and Google sessions I was already logged into. That's why it restarted the Discord client and Chrome. This allowed the scumbag to impersonate me and make changes to those accounts without having to take control of my laptop itself. That's also why he was able to keep doing damage after I cut the Internet off. This type of attack has been used beyond Discord and you can theoretically use it against any site that stores your login session with cookies. It's even been used to take over several prominent YouTube channels like Linus Tech Tips in the past.
Due to the how cookies work, this is not as easy a problem to solve as you might think, hence why it's been an issue so long. Google is developing an open-source framework called Device Bound Session Cookies to combat this for Chromium browsers (i.e. basically all of them except Firefox), but it's only been in closed testing to this point, though it looks like it might enter production soon.
You might be thinking that since I used the separate Discord client, how did he get in with a browser based attack? That's because Discord's client is literally its own browser. Enter Electron.
At its most basic, Electron is a framework that allows developers to make applications that aren't real applications, but just standalone Chromium browsers that load a web site designed to look like real software. Many developers like this because it makes it easy to port to multiple platforms since you're running a minimal amount of native code. Sounds good in theory but in my opinion, it's led to a bunch of poorly optimized, bloated, improperly secured applications that take an ineffective one size fits all approach, relying on a browser to do most of the work.
Since Electron apps are just browsers in disguise, they're also prone to the same security issues browsers are, including session hijacking. Not only is there no way to prevent those yet, but even when Device Bound Session Cookies become a thing, Discord will still have to integrate them as it doesn't just work out of the box. I hope they will as it will save them a lot of support tickets but you know what would also work? Writing a damn native app with its own safeguards and that retains session data in its own isolated storage!
Electron is a plague on modern software development and if used at all, should only be in specific, low-security scenarios where it makes sense, not as a cheap and lazy method to shit out cross-platform applications in a "move fast and break things" way where the very nature of your middleware makes breaching accounts something you can learn in an hour on YouTube.
When Everyone's Support Is Trash, No One's Is

Once I had the initial tide of damage contained, I could turn my attention to unfucking the situation.
I called my bank, disputed the fraudulent charge and had them issue a new card. That was thankfully relatively painless because well, companies care when it can impact their bottom lines too. Funny that.
I tried to email support for the scummy Roblox marketplace and while they said they would ban the account using my email from further purchases, they couldn't refund the one the scumbag already made as the item had been redeemed. How that's my problem I don't know, but I wasn't going to get anywhere with them.
From the support transcript, I had the name of the Roblox account the item was added to. I'm sure the scumbag doesn't play Roblox, he was just loading up an account with stolen high-value items to resell later. I opened a ticket with Roblox to try and have the account banned for illegal activity and they responded the following day acting like I asked a different question entirely. This was also no surprise. Roblox can't even make an effort to deal with the rampant child predators on their platform, what chance did I have that they'd care about this? Oh well, my bank will get me the money back.
Since I knew my Google Workspace was now safe, I was able to create another alias to make another Discord support account, then made a ticket with all the information I had in exhaustive detail to remove any doubt that I was indeed hacked and I kept adding more info as I got it. I quickly learned that even several years ago, Discord support was known to be among the worst anywhere, taking days or even weeks to even respond to tickets and often refusing to action them properly. The fact that I was a paying Nitro user with an account and server both over 7 years old? Doesn't mean a fucking thing.
Let me tell you, as an IT guy, I've dealt with some legendarily bad support, but never have I seen a company take weeks to respond to security incidents that could impact a large number of other users on their platform. The scumbag continued to try to propagate his scam to others and I had to rely on other friends to warn those I knew about. You'd think Discord would care about that, but apparently not. We'll get back to them.
While I settled in for a potentially long wait, I decided to see what else I could learn about the scumbag and what I could do to try and stop his scam.
I did nuke and pave my laptop, but took a copy of the malware and made note of the site he sent me to. To my utter shock, the malware showed green on every single available scanner on VirusTotal. I couldn't believe it, but I assume it must be getting generated by a tool that creates unique signatures for each instance.
I submitted the file to Microsoft for analysis and at time of writing, it's still "In Progress". Someone on Bluesky then suggested submitting it to Hybrid Analysis, an awesome tool that actually loads up a virtual machine, launches the malware in it and logs every interaction it makes with the system. This confirmed what it was in short order and gave me a ton of useful information to boot. It's a nasty piece of work it is.
Armed with this new info on top of what I already knew, I set to work trying beat down as many parts of this thing as I could. This post is long enough already so here's a rapid fire of what I did:
| Item | Vendor | Contact Method | Result |
|---|---|---|---|
| Website | Cloudflare (Pages.dev) | Abuse Form | Site killed, replaced with malware warning 👍 |
| File Host | Dropbox | Abuse Email | File still up 👎 |
| C&C(1) DNS Host | Cloudflare | Abuse Form | Domain no longer resolves(2) 👍 |
| C&C(1) Domain Registrar | Turkticaret.net | Abuse Email | Domain no longer resolves(2) 👍 |
| Email Address | Abuse Form | Email address still active 👎 |
(1) Command & Control domain, what the malware phoned home to for instructions.
(2) The domain still shows as registered and has Cloudflare DNS servers registered to it. Unsure which vendor is responsible for taking it offline.
I have to give Cloudflare credit here for actually taking action on my report and in less than 24 hours. That huge companies like Dropbox and Google still haven't done shit to action reports of their products being used for illegal activity is shameful, as is it being nearly 2 weeks later as I write this and Microsoft still hasn't validated the malware that Hybrid Analysis did in minutes.
So, let's get back to Discord. I couldn't do anything but wait, so I did. I knew from reports that it could be weeks until I heard back, meanwhile my account is getting more and more trashed as the scumbag tries to phish more people. Discord eventually responded after 8 days. That's much better than weeks, but still completely unacceptable for a security issue. It should have been and could have been 12 hours at most. Once I did get assigned a rep, she was actually quite helpful and responded quickly. It took another day, but I got control of both my main and support Discord accounts returned to me and could start rebuilding everything.
To count everything up, that's 2 (or possibly 3) cases of vendors taking appropriate, timely action and 6 who either took too long or have done nothing. On top of that, most of the ones dropping the ball are some of the largest companies in their industries, if not the world. These reports and others like them represent clear and present security threats to their wider user bases yet they can't be bothered to do shit or if they do, way too late. To see such large and critical Internet companies take such a lackadaisical attitude towards security is both shocking and depressing.
Lessons Learned For Me and You

As I said way up at the top of this tome, aside from the scumbag himself, the next in line for blame here is me for falling for his scam. From some conversations I've had since, it looks likely that this particular scam is part of a turnkey kit people can buy that quickly generates the malware, the fake web site and has all the steps they need to mount this kind of attack. My guess is the scumbag is probably someone in a poor country who is running scams to get by. That doesn't give him the slightest ounce of sympathy from me, but it's likely.
I can give you the usual spiel about not opening random files from people you don't know and blah blah blah, but you've heard that before. What I can tell you is that even though it sounds like a broken record, it's also still good advice because I've been in IT for 25 years, part of my job is teaching end users how to avoid getting scammed and I still fell for this. It can happen to anyone and us professionals may be better at avoiding it, but we're certainly not above it.
What really got me on the hook was that the scumbag was using another stolen account from an old school game developer I know and have talked to before and mimicked his mannerisms. I hadn't talked to this developer in months though and I should have clued in when he messaged me out of the blue asking what was up, but it was late at night and I wasn't thinking properly, so I didn't have my normal spidey senses activate when he asked me to go to a random web site to download a file from Dropbox.
If I were more with it, what I would have done first is run his installer through VirusTotal (which wouldn't have helped in this case), then I would have run it in a sandbox virtual machine I have, where I quickly would have noticed it didn't install a game, but which also didn't have anything installed he could have stolen sessions from. This would have got me onto his scam, but I skipped those steps and went straight to getting screwed. As my girlfriend will recount, I was cursing myself for hours after that. I wasn't so much stupid as lazy, which can be just as dangerous.
So what can you dear reader and likely non-IT person do to avoid this yourself? Honestly, if you set your default position to be even more paranoid than mine, you can do so easily. Here's some quick tips:
- If you're asked to install a game and it's not on a recognizable digital platform, just don't. Ask the person to put it on somewhere like itch.io that's free, but requires some effort. If it's a developer you know, ask them to send a link to the file to your email, but don't tell them what your email is. If they're legit, they should know it.
- If you do download the file, run it through VirusTotal and Hybrid Analysis before doing anything else. As I showed above, a green light from just one isn't enough. If either one shows red flags, refuse to run it. If the person says it's a false positive, tell them to fix it and send it to you again.
- If you have the means, run the file in a virtual machine that has nothing else loaded in it first and make sure nothing strange happens.
- If you sense the slightest thing is off after running the file, immediately take your computer offline. Put it in airplane mode or disconnect the network cable and don't hesitate.
- For the love of everything, use MFA and passkeys everywhere you're able to, and use a password manager to generate random passwords for each site. I recommend Bitwarden, but there are many others. I know it's a hassle, but it will save your ass when things like this happen.
- Never expect that support will have your back or that if they will, that they'll be quick about it.
If all this sounds like too much effort, then skip every step except the first one. Remember that even if the person contacting you is legit, you're the one doing them a favour and if they really want your feedback, they'll do what's needed to make you feel safe providing it. If they make excuses or try to handwave away your concerns, just say no. Anyone who takes offense to you wanting to avoid malware is someone who doesn't deserve your time. Harsh, but true.
Discord, Get Your Shit Together

This is the most important part of the post for me, not just for the catharsis of ripping Discord a new one, but because this could be avoided for so many with some key changes on Discord's part. Some are relatively minor and some are not, but they are all necessary to ensure it's properly secure:
- Require all changes to account settings to reauthenticate MFA every time. This is already done on a ton of other services and it's insane it isn't required on Discord.
- Impose a cooldown period on changing account email addresses. No one with a legit reason to do so needs this done instantly. Make the user wait three or more hours after confirmation before applying the change.
- Once an account is stolen, why can a user not use one of their MFA recovery codes to take it back? Even if the attacker has their base MFA key (and the scumbag didn't in my case), recovery codes don't rotate and are supposed to be kept secure and separate. They would allow a reasonable baseline of identity verification.
- There should be a "break glass" procedure for servers. In the event an account's MFA token is captured and changes are made, there should be a secondary way for an admin to prove their identity, just to lock that account out while they try to recover it. Again, this is common practice on other services. That I have to consider making a separate account that has no purpose other than being a demarcated admin for my server is ludicrous.
- Either hire more support staff or leverage AI for account recoveries. There is no excuse for people having to wait a week or more to have their tickets looked at in the case of an account compromise. None. This is a callous disregard of the needs of both those compromised and those the attackers go after in their names while they wait on you. I'm not even a big AI advocate, but an agentic workflow could easily be designed to allow a user to immediately provide the info needed to verify their identity. The model could then just request a quick human review and approval and once provided, take all the necessary actions automatically. This would allow speedy recoveries without extra staff or waiting.
- Finally and most importantly, ditch Electron. I don't care how much more work it would be to make a proper native app for each platform. You have the means so get it done. Using an easily exploited browser base instead of making a real app is lazy, cheap and negligent. This might have been OK when the platform was a scrappy startup (though I'd argue it wasn't even then), but now you have no excuse. A proper codebase that undergoes regular hardening and security audits is a no brainer at this stage and your continued insistence on using a browser framework is doing a massive disservice to the users who built and maintain your monopoly.
This is a company that's likely going public soon and that I'm certain has never turned a profit. They're going to be pressured to cut corners and further enshittify their monetization as soon as the stock starts trading, but with going public also comes more eyeballs on you when bad things happen. You see what's been happening to Roblox's reputation the last while? You already get a lot of shit in the press for your lax moderation and the kind of communities you let thrive on the platform. That plus a high number of account breaches because of your shit codebase and policies isn't going to do you any favours.
The time to fix your shit is now, not after you go public and certainly not after you start making waves in the media. Inveseting in security now will ultimately lower costs later, both tangibly in terms of support and intangibly in terms of perception and your users thinking you actually care about them. Because I can assure you, not many do right now.
Conclusion
I'll keep using Discord for now because there's really no other viable alternative. I hate that this is the case, but it is for the moment. I will be cancelling my Nitro though and certainly don't intend to give this company another dime of my money until they can better demonstrate that they've earned it. Right now, the platform is showing itself to be the inevitable result of what happens when a lack of competition results in a monopoly player.
Discord revolutionized how initially gamers, but now non-gamers communicate and in general, I think it's a great platform. They can fix these problems and will if enough users hold them accountable. Without us, they've got nothing to sell when they go public and it doesn't take a ton of us making noise for them to take notice. Demand that they take security seriously and not take us for granted.
Stay safe out there and well, join my community I guess?




